Executive Insights on Cyber Security – August 2018

CFOs know it’s hard to manage what isn’t measured. So we have partnered with Cyber Rescue to track monthly developments in the cyber security posture of large enterprises, as well as key developments in cyber regulations and breaches.
This month’s developments in Cyber Security Postures
The below graph for August is generated using the very powerful Security Scorecard platform. Our members often use it to comply with article 32 of GDPR, to regularly evaluate the effectiveness of security measures at their information processors (ie suppliers).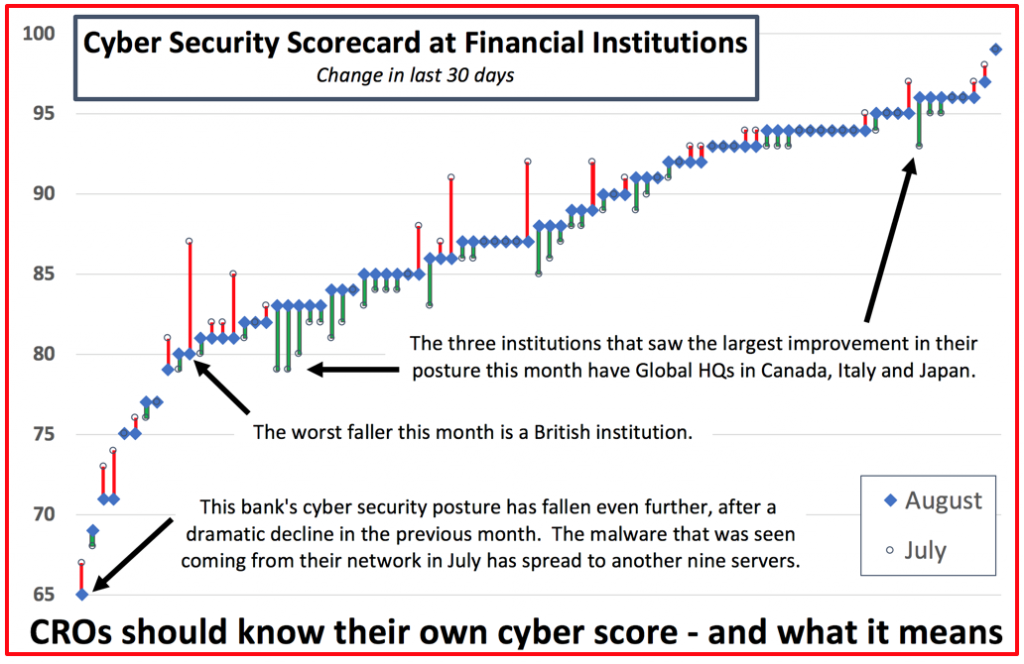
Cyber Security Scorecard at Financial Institutions
At a minimum, CFOs can use the detail in their own monthly Scorecard to engage effectively with their IT colleagues.
Some executives are unaware how fast cyber vulnerabilities can arise.
We therefore track changes in what hackers can see at various organisations.
Our August review is of Financial Institutions.
The lowest-ranked banks and insurers have been compromised by malware, or have serious vulnerabilities on encryption and similar defences that are visible from the outside.
This month’s developments in Cyber Regulations and Breaches
Your cyber recovery plan "may be too large,” according to the European Central Bank, after reviewing over one hundred such documents.
The shortest plan analysed by the ECB was less than 80 pages, the longest was over 1,700. “The ECB is doubtful that every bank’s plan could be implemented in an effective manner.” The ECB list best practises, such as short Play Books and Dry Run Exercises (which Cyber Rescue specialises in).
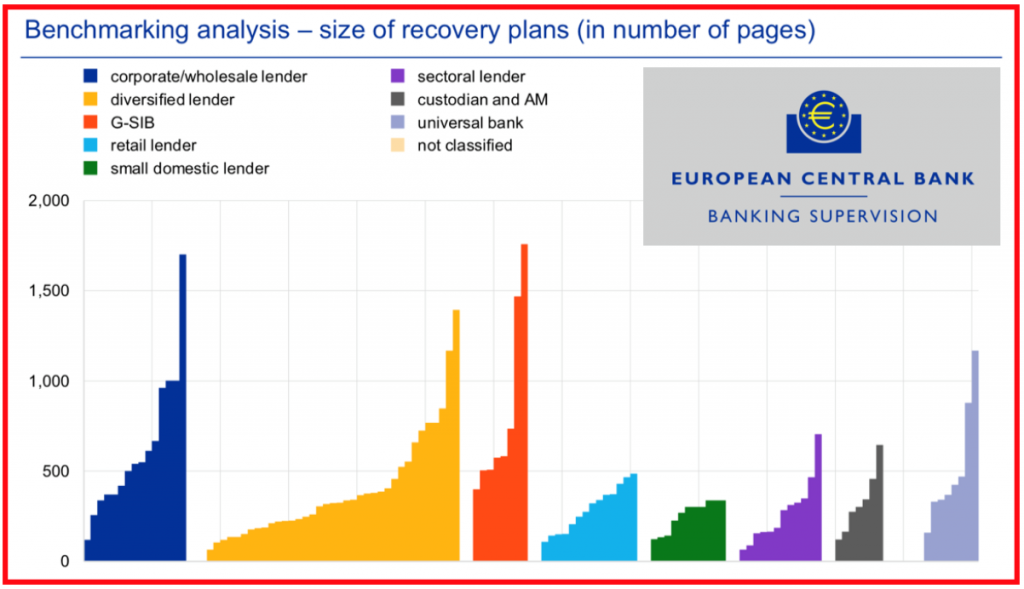
Practicing those recovery plans is part of what the “Threat Intelligence-based Ethical Red Teaming” initiative (TIBER-EU) is all about.
While voluntary, many banks and regulators worldwide will spend some of the summer re-reading its intelligent approach. A good summary is here.
Similarly, “what you do after you’re attacked” is the main cyber concern of the Singapore State investment fund, as reported in the FT.
To help recovery after a major attack, the USA’s new Cyber-Risk Management Center will be launched by Government to protect banks, energy companies and other national critical infrastructure providers across America.
New research continues to highlight how cyber crises could be inflicted, for example showing that over 5% of security professionals have considered working for criminals, and that corporate networks could be hacked via fax machines.
Cyber crises are prioritised in a July paper by the Bank of England, which says “Boards should be planning on the assumption that disruption will occur.”
A focus of the Bank of England paper is supplier risk, eg that “Boards’ oversight needs to cover any activities outsourced to third-party providers” (suppliers).
Building the UK financial sector's operational resilience
The 200% increase in Supply Chain compromises was highlighted by UK’s NCSC on 19th July. Similarly, the USA’s NCSC reported how hackers are targeting software supply chains, referencing 2M computers infected because they purchased CCleaner anti-virus software. Crowdstrike reported that 68% of security experts know they’re unprepared to defend against supply chain attacks.
Apple’s Chief Risk Officer is among those considering the supply-chain resilience lessons of the $170m harm caused on 3rd August to their supplier, by a WannaCry variant on unpatched machines.
A supplier breach was admitted by TCM Bank on 3rd August, hitting credit card applicants in the US. Another supplier breach hit National Australia Bank and Macquarie Group, via HR Cloud provider PageUp in June. Similarly, the small bank Monzo and digital banker Revolut were among those hit by a breach at survey supplier Typeform.
Thailand, India and Russia saw more direct breaches and fraud, at Thailand’s third largest bank, the State Bank of India and at PIR Bank. The Russian breach cost $1m USD, and was blamed on PIR Bank still using an out-of-date router. A more recent risk to financial institutions is demonstrated by IntSights’ finding of a 135% annual increase in the bank data for sale on dark web markets.
Cyber insurance prices are falling, with CIAB reporting that 30% of insurers are suffering cyber prices decline, versus 12% enjoying an increase. The percentage of enterprises buying cyber insurance is flat, though half of companies that renew their cover increase it, typically to $3.2 million. The insurance industry has defined shared terminology, with a 9th July announcement of a Cyber Data Breach Standard. Perhaps Virginia Bank wishes the Standard was in place before its $2m dispute with its cyber insurer. More on insurance here.
The cost of the typical data breach has risen 6.4% according to the annual Ponemon survey, and now stands at $3.86 million (with wide variation by country and sector). Interestingly, the typical enterprise is estimated to have a 28% chance of suffering “a material breach” in the next 24 months.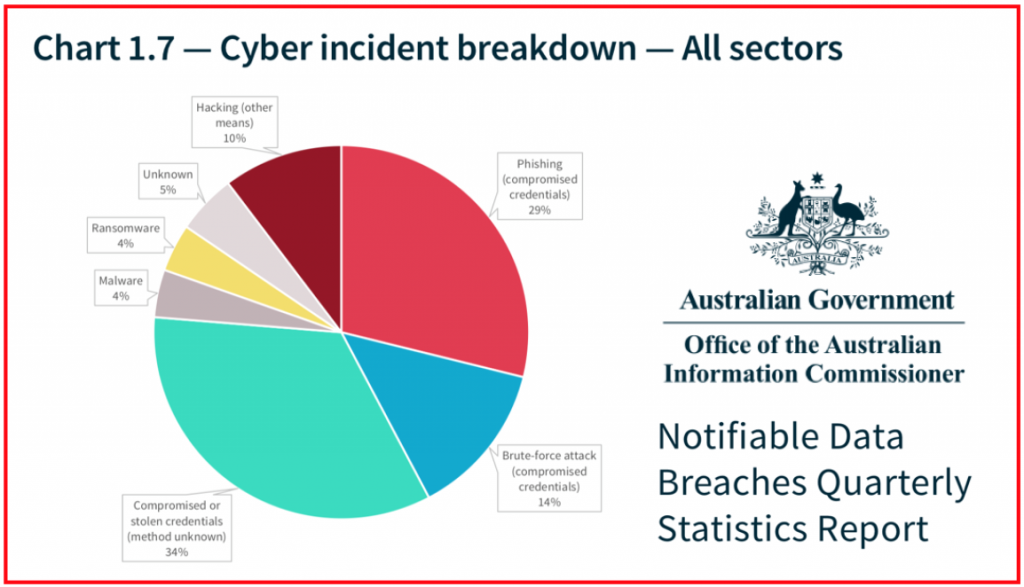
Cyber Incident Breakdown - All Sectors
Data breach reports are increasing, eg they are up by 63% in Australia in the 3 months.
Breach reports quadrupled in the UK and quintupled in Ireland after GDPR came into force, with over-reporting a new concern for regulators.
These breach reports provide good threat intel, eg that in the finance sector, 50% of breaches are now caused by Phishing.
Cyber targets are changing, eg with a “dramatic increase in interest in exploits for SAP apps” reported by Digital Shadows on 23rd July, but a cooling in CryptoMining reported by Malwarebytes.
Cyber Rescue is Europe’s leading specialist in helping executives lead business recovery when cyber defences are breached. Check out more here. Kevin welcomes feedback: Kevin.Duffey@CyberRescue.co.uk
Like to hear more on this topic, in person? Why not attend the AICPA & CIMA Cyber Security Conference in New York or London.
Kevin Duffey will be speaking on day one of the AICPA & CIMA Cyber Security U.S. Conference during his session: 'So you're under attack: Simulating the financial and business impacts of cyber attack'.