The human factor: Educating and enabling your workforce to effectively combat cyber threats

Cyber risk remains a top concern among CROs, while human mistake remains the top cause of cyber incidents such as breaches. To arm their workforce, many companies do various training, but Brian Byagaba, formerly of Commercial Bank International (CBI), argues, that maybe this method is not effective enough. In this article, Byagaba shares an alternative method of communicating with staff and an alternative way to measure your cyber resilience.
Recent research by security firms continually supports the argument that humans are the weakest link when it comes to cyber security. What is shocking, however, is how many of the security incidents are due to human omission/ commission. According to McKinsey & Company a staggering 50% of all data breaches between 2012 and 2017 involved insiders in the very organisations that got compromised. It is not hard to understand why this number is so high, when even the latest Verizon Data Breach Investigations Report shows that just over of 33% of attacks in 2018 alone included social engineering techniques. For the Verizon report, it is worth pointing out that social engineering techniques refer to all forms of bait that are intended to hook the human into carrying out an action that they would not have otherwise performed; giving up a password, confidential information or even remitting funds directly to the con artist. Cyber criminals are commonly using bait such as phishing emails, dubious phone calls or text messages and correspondence using social media. You may also be surprised to know that these techniques still work, which is why even with incredibly sophisticated malware making news headlines, a smart criminal will naturally start with the easiest of social engineering techniques. Only when they fail does s/he need to work their way upwards to more sophisticated methods.
So, since we know social engineering is such a high contributor to security incidents, it should come as a surprise to know that on average banking and financial services firms invest only 5% of their security budget on security awareness; this is according to the 2018 SANS Security Awareness Report. Cost here not only means money but also time, which it turns out is the most valuable of resources when it comes to security awareness. In fact, 76% of the respondents to the SANS survey either did not know or couldn’t share how much they actually spent on security awareness. SANS has proposed a good way to measure security awareness maturity from non-existent (no resources are allocated) through to a robust metrics framework. Three years ago, we found that our very own Commercial Bank International (CBI) invested just over 4% - not that different from other banks of similar maturity.
What isn’t immediately obvious is how banks compare to other industries. When looking at the highest level of maturity (that is the robust metrics framework), banks fared a lot worse, with less than 4% of firms at this level. Viewed another way, 80% of banking and finance firms are operating at a level of maturity driven by the need to be at least compliant with regulatory requirements. It would be misleading to assume though that banks are a homogenous cohort, and therefore a cookie-cutter way of advancing security awareness would be effective.
Commercial Bank International, for example, has 500 employees from 35 countries as far apart as Argentina, Canada, Portugal, Tanzania, Philippines, Australia, and of course United Arab Emirates. There is no silver bullet to building a sustainable security culture when how we are wired is so diverse. Thankfully, we are more alike than we are different. We have taken a less conventional approach to looking at staff, in many ways drawing parallels with our understanding of computers. The human brain behaves a lot like a computer, complete with an ‘operating system’ (OS) that stores, processes and transfers information just like computers do. Dr Joe Dispenza author of ‘Evolve your brain: The Science of Changing Your Mind’ puts it well saying that “Our brains are the hardware that runs the software that is our mind.” There are, nevertheless, big differences between the human brain and a computer; for starters we cannot exactly upgrade our brain and no two brains are identical. According to recent neuroscience research, however, there are certainly ways to enhance the brain’s capabilities without needing to physically change it. But that is a wide subject for another day.
The traditional approach to upgrading the Human OS assumes a fixed mindset; whereby security awareness material must be drummed into people for it to be effective. This typically had mandatory (computer based) training delivered annually and focused on ensuring that employees knew the correct answer to pass an assessment. This was a one size fits all method. If your firm still does this, all is not lost, at least you are doing something to help your employees remain aware. A more effective approach in recent times assumes a growth mindset. Employees are more frequently engaged with a shorter feedback loop that recognises there is a range of possible correct answers to a question. The focus is on rewarding positive behaviour and training is personalised to address staff in their unique context; sensitive vs non-sensitive roles, technical vs non-technical teams, senior vs junior grades, customer vs non-customer facing, etc.
At CBI, we quickly identified the important touch points with staff, for example using phishing simulations, contests, roadshows, brownbag sessions, chat channels (we used Yammer from Microsoft) and yes, even washroom posters. It turns out that washroom posters got the most traction as we invaded the people’s ‘last happy place’. We did not start out knowing which would be the most effective medium especially with such a diverse ethnic mix and that is why experimentation played such an important part of our approach. The difficult part was measuring through the cycle which methods were positively moving the security awareness needle. These results were only evident over an extended period with the impact increasingly apparent a year later.
Albert Einstein once said “Not everything that can be counted counts, and not everything that counts can be counted.”
We therefore continually refined how we measured success and listened closely to employee feedback especially for what they are not saying. We have learned for example that staff are more likely to complain about something they do not like than praise something they enjoyed.
As an example of how impactful changing the measure can be, we can look at how CBI’s phishing simulation results have evolved over time. We used to measure the security awareness programme by how many staff fell for the simulated phishing emails – that is, either clicked on an embedded link or opened the attachment – doubling down on repeat offenders and pushing to achieve lower failure rates. This worked for a while to get failure rates falling but what exponentially changed the game was when we inverted our thinking and introduced a report phishing email button and started focusing on the number of people notifying information security of the suspicious emails. As shown in the chart below, we continued to see better results and we now measure how quickly staff report a unique phishing email. Reducing the mean time to detect malicious activity has greatly improved our ability to respond to threats; the IS team now feels like a 500-strong team. How long will this positive trend continue? We do not know for sure. What we do know is that we will continue experimenting to find better ways to empower bank staff to respond to evolving cyber threats.
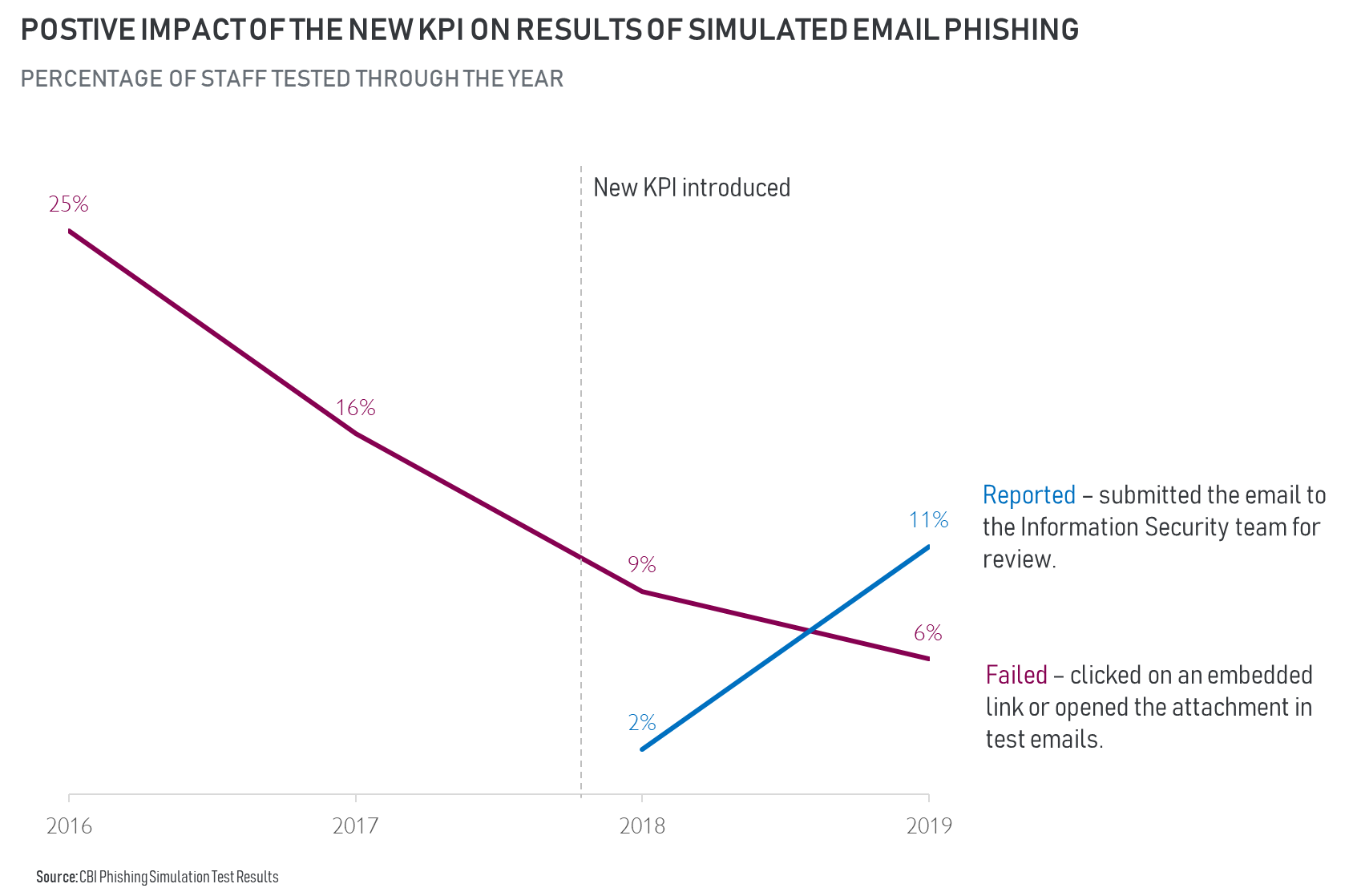
If you aren’t already experimenting, there is no better time than now. The cost to trial many of the techniques is low and the various service providers have ready content that can be easily customised. We also found that by bringing out the human side to cyber security we were more approachable for other policy related queries that staff want answered. With such a high frequency of targeted social engineering attacks on employees it is vital that we increase our level of investment, both time and money, in strengthening the human defences. When was the last time you upgraded the human OSes in your organisation?
Brian Byagaba now leads a Fintech startup, Pattamar, based in Abu Dhabi, UAE, that is taking a new approach to addressing the pains of cross border payments. See www.pattamar.com for more.